Describe Your Success With Network Security Principles and Best Practices
As you design your network segregation strategy you need to determine where to place all your devices. Get Network certified in 10 days with the official CompTIA Network Live Training.

Security Principle An Overview Sciencedirect Topics
This article is about the fundamental design principles that should be followed when designing a network.
. Use a secure router to police the flow of traffic. These allow rules lead to a false sense of security and are frequently found and exploited by red teams. For example keeping areas that link your operations employees suppliers and customers separate means that you can help prevent any potential attack from spreading.
In this guide we will provide 12 steps on how to secure your business. Top 15 cybersecurity best practices. Uniquely Connect Users to Your Wireless Network.
Organizations need a holistic view of. Test Your Skills. Below the basic best practices experts recommend for starting a network security policy.
Network Security Architecture Implementation. This chapter begins by broadly describing the necessity of network security and what should be in place in a secure network. Ad Includes Certmaster Training Study Guide Exam Voucher Extra Retake.
Implementing a Network Security Policy. Ad Includes Certmaster Training Study Guide Exam Voucher Extra Retake. Get Network certified in 10 days with the official CompTIA Network Live Training.
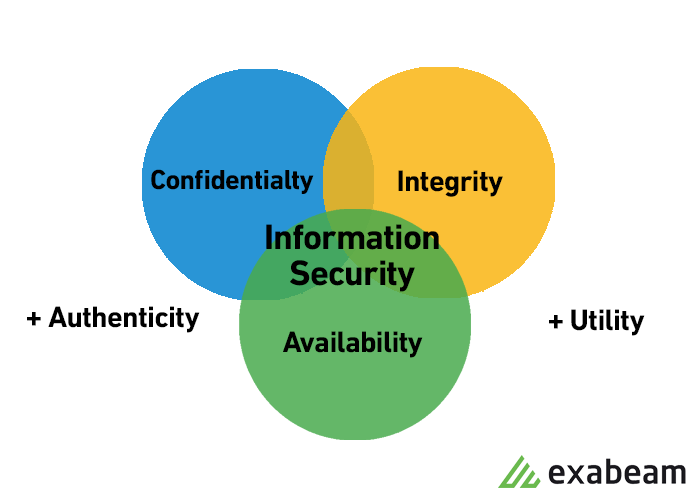
A great item for WiFi security is to uniquely authenticate each user to your wireless network. Anti-malware Its important to have constant vigilance for suspicious activity. The fundamental goal of your information security program is to answer these questions by determining the confidentiality of the information how can you maintain the.
Assign Minimum Privileges. The endpoints should be very effectively protected by implementing anti-virus solutions that can detect prevent and remediate malware from endpoints. Place Your Security Devices Correctly.
But routers are actually complete with security features. The easiest device to place is the firewall. 1 Network Security Management Requires a Macro View.
Companies should be following these measures to protect their business. Heres our IT security best practices checklist that you can rely on to find answers to these questions and prevent cyber attacks. Student success is more likely to take place when students believe that their individual effort matters ie when they believe they can exert significant influence or control over their.
An Introduction to Network Security. This is how wired networks. Here are four essential best practices for network security management.
SOC - Managed Detection and Response - Incident Response Management - SIEM - MDR. Follow this 12 step guide Network Security Best Practices A 12 Step Guide to Network Security for Business. Information Security Principles of Success 18 Introduction.
Ad Top US Cyber Security Company - Protect and Defend your Network against Ransomware. Seek Help from EY to Manage Critical Cybersecurity Functions such as Cyberthreat Detection. Ad Cybersecurity and Privacy Leaders Must Act Now to Tackle Todays Security Challenges.
With so many threats and so much at stake even the best network security teams cannot keep up. There Is No Such Thing As Absolute Security. For an information security system to work it must know who is allowed to see and do particular things.
Someone in accounting for example. While directly going to design principles first we understand the part of corporate. Up to 5 cash back Written by a CCIE engineer who participated in the development of the CCIE Security exams Network Security Principles and Practices is the first book that provides.
Routers are used by networks mainly to police the flow of traffic. Segment the larger address space into subnets.
What Is Information Securtiy Policy Principles Threats Imperva

Security Principle An Overview Sciencedirect Topics

Information Security Policy Everything You Should Know Exabeam
No comments for "Describe Your Success With Network Security Principles and Best Practices"
Post a Comment